Just for those interested, here’s the screenshots of the ADFS installation on a Windows 2012 R2 Preview installation. Before 2012 R2 it wasn’t advised to install ADFS on a domain controller as the ADFS solution relied on IIS. But with the 2012 R2 version the IIS dependency is gone and Microsoft recommends installing ADFS on domain controllers. I think this will lower the bar for a lot of companies. Also the enhanced authentication options (multi factor) seem really promising.
The installation:
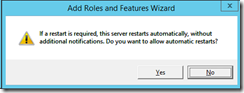
Remark: in the end my system didn’t need to reboot
The configuration:
Remark: small sidestep here: obviously I want to use Group Managed Service Accounts!
Remark: lab only procedure: ensures Group Managed Service Accounts are available immediately
The management console with the focus on the new Authentication Policies section
A new Relying Party Trust type:
If I read the explanation correct this will allow you to publish non claims-aware application over the new Web Application Proxy role.
Remarks:
- The option for a stand alone ADFS server is no more. Either you install a single node farm or you install a real farm. Makes sense to me.
- You still have the option to choose between a Windows Internal Database or a dedicated SQL Server database. This might be a hard choice. I’m not sure I’m happy to have Internal Databases running on my domain controllers. The SQL on the other hand requires a cluster for proper availability which might be quite expensive to sell to your customers.
- Named certificate forces you to take the subject of the certificate as the Federation Service Name. Wildcard certificate allows you to pick freely as long as the wildcard is respected. It seems you can have additional . in the wildcard part though. I advise against this as you’ll probably face certificate validation errors in your browser. Example: *.realdolmen.com allows you to select sts.sub.realdolmen.com.
- More on Group Managed Service Accounts: vankeyenberg.be: Why you need group managed service account and how to use them and Ask PFE Platforms: Windows Server 2012: Group Managed Service Accounts
- If you want to compare=: the Windows 2012 ADFS installation: vankeyenberg.be: ADFS Part 1: Install and configure ADFS on Windows 2012
- The Authentication Policies section in the management console seems awesome. Very clear and it seems very easy to manage.


























3 Response to Windows 2012 R2 Preview: Active Directory Federation Services Installation Screenshots
Can you point me to a link on the Microsoft Site that says "Microsoft recommends installing ADFS on domain controllers" ? We are looking at this question currently but cannot find in their best practices for ADFS 2012 R2 that installing on a DC is recommended.
Thanks for your help!
John
I'm sorry for the latish response.
When 2012 R2 was about to be released I heard that statement somewhere. I did a quick google and couldn't find it. There are several people saying that you should NOT do it, but they all use the argument "ADFS relies on IIS" and IIS on a DC is bad idea. Which I agree 100% with.
On the other hand ADFS on 2012 R2 no longer uses IIS, so that argument is out... Another one is redundancy. If you want two ADFS servers and you want to load balance them you can do that with a Hardware LB or Windows NLB. Using Windows NLB on a DC is not something I would advise for.
All in all you have to check the size/complexity of your environment. ADFS rights are typically issued through local admin rights on the ADFs servers. If you put ADFS on your DC your ADFS admin has to be (more or less) domain admin. So I'd say compared to ADFS on 2012 (and lower) you can justify installing it on a DC. Doesn't make it the only way to go forward though.
On a side note about putting it on a DC. I was just reading this article: https://technet.microsoft.com/en-us/library/hh831502.aspx and it is stated as a feature of the simplified deployment experience.
Add Your Comment