To be completely honest this subject has been blogged a lot in the past. However just this Friday I helped a colleague which was having issues setting up DNS aliases for SQL. He seemed to have troubles connecting his Management Studio to SQL. And today I could use the information again when working at a customer which was having issues authenticating to his webserver. So I believe this is still solid information to spread.
So if you hit google with "disableloopbackcheck windows 2008 R2” you get quit some results. And if you search the official KB articles, this registry setting is referenced a lot when dealing with Access Denied errors locally on a machine. All these scenario’s have one thing in common: someone or some service is trying to access a service under an alias and this from on the machine itself.
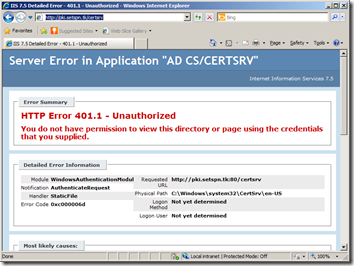
Simple example scenario: you set up Active Directory Certifcate Services and you choose “pki.contoso.com” as an alias for your Certificate Authority server. After configuring this record in DNS, you try to access this website http://pki.contoso.com/certsrv on the CA itself in vain. After trying to provide correct credentials multiple times it just fails. You are getting that nasty “HTTP Error 401.1 – Unathorized You do not have permission to view this directory or page using the credentials that you supplied”. Accessing this from a remote workstation using the same credentials works just fine.
If this is your problem, are it sounds similar, then this is your solution:
- kb926642: You receive error 401.1 when you browse a Web site that uses Integrated Authentication and is hosted on IIS 5.1 or a later version
- kb926642: Error message when you try to access a server locally by using its FQDN or its CNAME alias after you install Windows Server 2003 Service Pack 1: "Access denied" or "No network provider accepted the given network path"
- kb887993: Users experience authentication issues when they access a Web page in IIS 6.0 or query Microsoft SQL Server 2000 after you install Windows Server 2003 Service Pack 1
- kb914060: A logon window appears in Windows Server 2003 Service Pack 1 NLB when you try to browse the virtual NLB cluster name
- kb971382: Errors when crawling content sources in SharePoint Server 2007: "Event ID 2436" and "Access is denied"
And the list goes on. The workaround is very easy and active immediately: just create a REG_DWORD called DisableLoopbackCheck below HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Lsa and give it a value of 1
One of the articles actually references the DisableStrictNameChecking registry key. I remember setting this one when accessing a share didn’t worked when using an alias. Must but it’s older brother. Here’s an explanation: kb281308: Connecting to SMB share on a Windows 2000-based computer or a Windows Server 2003-based computer may not work with an alias name The reason we’re probably hearing this one a lot less is because since SMB 2.0 (Windows 2008 and up) this is no longer required.






1 Response to Access Denied Using An Alias
FIX: http://winplat.net/2015/10/26/error-accessing-file-shares-using-alias-cname/
Add Your Comment