One of my customers had problems with certain users being member of a lot of Active Directory groups. This resulted in several client side issues. There’s an easy and well-known “fix” for that: raise the MaxTokenSize registry key on all Windows operating systems in your domain. On Windows 8(.1) / 2012 (R2) the MaxTokenSize is already at its maximum (advised) value out of the box. That value is 48.000 bytes. In order to mitigate these users their access problems we raised the MaxTokenSize to 48.000 bytes on all clients and servers that are running Windows 7/ Windows 2008 R2. After this change the typical issues were gone. However new ones came up:
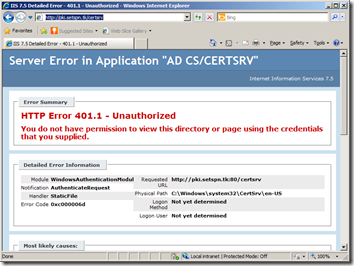
From time to time, when HTTP is involved, issues were encountered:
- Opening the Direct Access management console (depends on WinRM)
- Open the FIM Portal
- Streaming App-V packages over HTTP
- …
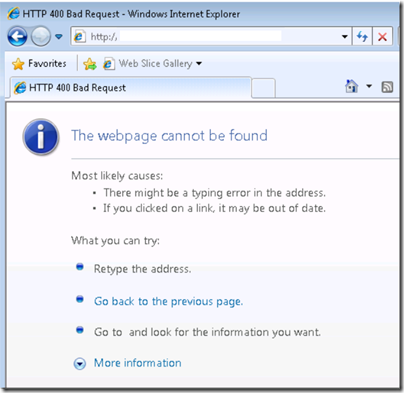
Typically the user would receive several authentication prompts and even after specifying valid credentials another prompt would reappear. Example browser based issue:
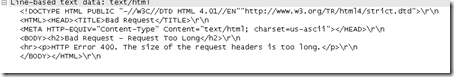
As you can see the browser gives an HTTP 400 Bad Request error. Using a network trace we can easily see why it’s considered bad:
And the packet details:
The details clearly state that The size of the request headers is too long.
The problem here is that the token is allowed to be up to 48.000 bytes where it used to be 12.000 bytes. The http subsystem of a windows server has several parameters that are supposed to protect the server from oversized requests. However, as the token can now be a lot larger, the maximum request size has to be tuned as well:
From: KB820129
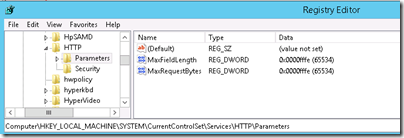
Below: HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\HTTP\Parameters there are two interesting values:
And from: KB2020943 we can find a formula to calculate the MaxFieldLength to set based on the MaxTokenSIze.
If MaxToken is 48.000 bytes (default in Windows 2012 and configure by GPO for 2008 R2/ Win7):
- (4/3 * 48000) + 200 = 64200
We’ll use the maximum allowed value of MaxFieldLength 65534 (=~ 64200) to allow tokens up to 48000 bytes. We’ll also use this value for MaxRequestBytes.
- MaxFieldLength: we can take the maximum allowed value: 65534
- MaxRequestBytes: 65534
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\HTTP\Parameters
Other useful information:
I specifically wanted to post this information as in many other only articles/posts I always see people just using the maximum allowed value for MaxRequestBytes and I don’t feel 100% comfortable with that. Second, in my opinion it’s advised to have these values pushed out to all your server systems. Especially now that Windows 2012 and up have a MaxTokenSize of 48.000 by default. If you don’t push these HTTP.sys parameters, you’ll end up troubleshooting the same phenomena multiple times from different angles. Why waste time?






































1 comments