[Update 21/12/2010] This topic was discussed on the FIM TechNet Forums as there’s some official Technet Documentation out there now, I would like to reference here. For a fully supported Kerberos enabled CAS array, Exchange 2010 SP1 is required, and you can follow this guide: http://technet.microsoft.com/en-us/library/ff808313.aspx
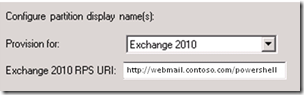
One of the problems I had with FIM 2010 in the past is the configuration of the RPS URI in the FIM Active Directory Management Agent (AD MA) configuration. When you want FIM to provision mailbox’ for you, or when using FIM for GALsync (provision contacts) you have to provide the URL to the exchange PowerShell webservice (http://webmail.contoso.com/powershell):
A lot of Exchange environments have more than one CAS server, typically these are combined with a NLB solution. So ideally you just point FIM to the CAS URL (like webmail.contoso.com) and thus ensuring FIM will not be dependent on the uptime of one specific CAS server. Because the MA only uses Kerberos to connect to that URL, there is a problem. Out of the box the CAS array URL is not kerberos enabled. As such the provisioning of mailbox’ will fail. When targeting a specific CAS server Kerberos authentication goes just fine. Because all required SPN’s are registered for each CAS server by the exchange setup and thus Kerberos authentication against a CAS server works.
From Exchange 2010 RU3 (Or RU4, not quit sure) there is a way to enable the CAS array for Kerberos. The word is out that this would officially be supported from Exchange 2010 SP1. The following steps are required:
- Create a service account in Active Directory: svc_exchange
- Register the SPN’s on this account (I always register both FQDN and short):
- setspn -F -S exchangeMDB/webmail.contoso.com CONTOSO\svc_exchange
- setspn -F -S exchangeRFR/webmail.contoso.com CONTOSO\svc_exchange
- setspn -F -S exchangeAB/webmail.contoso.com CONTOSO\svc_exchange
- setspn -F -S HTTP/webmail.contoso.com CONTOSO\svc_exchange
- setspn -F -S exchangeMDB/webmail CONTOSO\svc_exchange
- setspn -F -S exchangeRFR/webmail CONTOSO\svc_exchange
- setspn -F -S exchangeAB/webmail CONTOSO\svc_exchange
- setspn -F -S HTTP/webmail CONTOSO\svc_exchange
- The following steps have to be executed on each CAS server
- $cred = get-credential "CONTOSO\svc_exchange"
- Set-clientaccessserver -Identity CASserver -AlternateServiceAccountCredential $cred
- iisreset
- restart-service MSexchangeAB
- restart-service MSexchangeRPC
- To verify the setting, execute the following on each CAS server
- Get-ClientAccessServer -Identity CASserver -IncludeAlternateServiceAccountCredentialStatus |fl AlternateServiceAccountConfiguration
From now on, if you use outlook to connect to the CAS array, or just when provisiong with FIM and using HTTP, Kerberos will be used. You can eassily verify this with Klist (Windows 2008 and up built-in) or with Kerbtray. Or just in the security eventlog of a CAS server.
The actual procedure I used comes from the following blog: TUTORIEL: Exchange 2010 SP1 (Beta) - Activer Keberos pour un pool de serveurs CAS (Client Access Array) As it’s French, I think it’s justified to have some English alternative.
Technet help for the set-clientaccessserver command: http://technet.microsoft.com/en-us/library/bb125157.aspx






7 Response to Exchange 2010 Enable Kerberos On CAS Array
It's now official :)
http://blogs.technet.com/b/exchange/archive/2011/04/15/recommendation-enabling-kerberos-authentication-for-mapi-clients.aspx
Hi Thomas,
Know that there is an issue with the /OAB vdir when enabling Kerberos against a generic/load-balanced Fqdn for Web Services...
I'm talking about that here:
French: http://unifiees.blogspot.com/
Automatic English translation: http://www.microsofttranslator.com/BV.aspx?ref=IE8Activity&a=http%3A%2F%2Funifiees.blogspot.com%2F2011%2F04%2Finfo-ou-lon-reparle-dexchange-2010-sp1.html
And Ross Smith IV has updated the guidance accordingly in the night (too bad my blog post was in Draft mode ;)):
Update 4/26/11: This post has been updated to include additional steps to ensure Kerberos authentication can be used for OAB downloads by domain-connected Outlook clients.
Thanks alot for bringing this to our attention! Definately something to look into.
Thomas,
Do we need to configure the MA to use the Exchange service account or that is not needed?
Sam
Sam, this is definately NOT required. You can just use "any" service account which you designate as the AD MA service account. Provide it read/write permissions on your AD OU's/objects as needed and add it to the Exchange groups which provide you the permissions to mailbox-enable objects.
If you got other questions, shoot ;)
Good luck!
Regards,
Thomas
Is this still required for Exchange 2013 if you point FIM at your load balancer name you have for OWA?
I'm not sure. Haven't encountered any Exchange 2013 setups at any of my FIM customers...If I were to guess I'd say it's still required. I would look up specific documentation for Exchange 2013 and Kerberos though.
Add Your Comment